leeholm16 in LNK file forensic artifacts
Once in a while, I’ll stumble on a question online (or get an email) from a person wondering “Who the heck is leeholm16?”
If you’re reading this post, you’re likely one of them :)
I never know exactly what situation leads people to ask the question, but they’ve invariably started using a forensic parsing tool against Windows PowerShell.lnk or Windows PowerShell (x86).lnk. For example, here is the forensic analysis of the LNK file included in a SANS408 course. It comes from lp.exe by TZWorks.
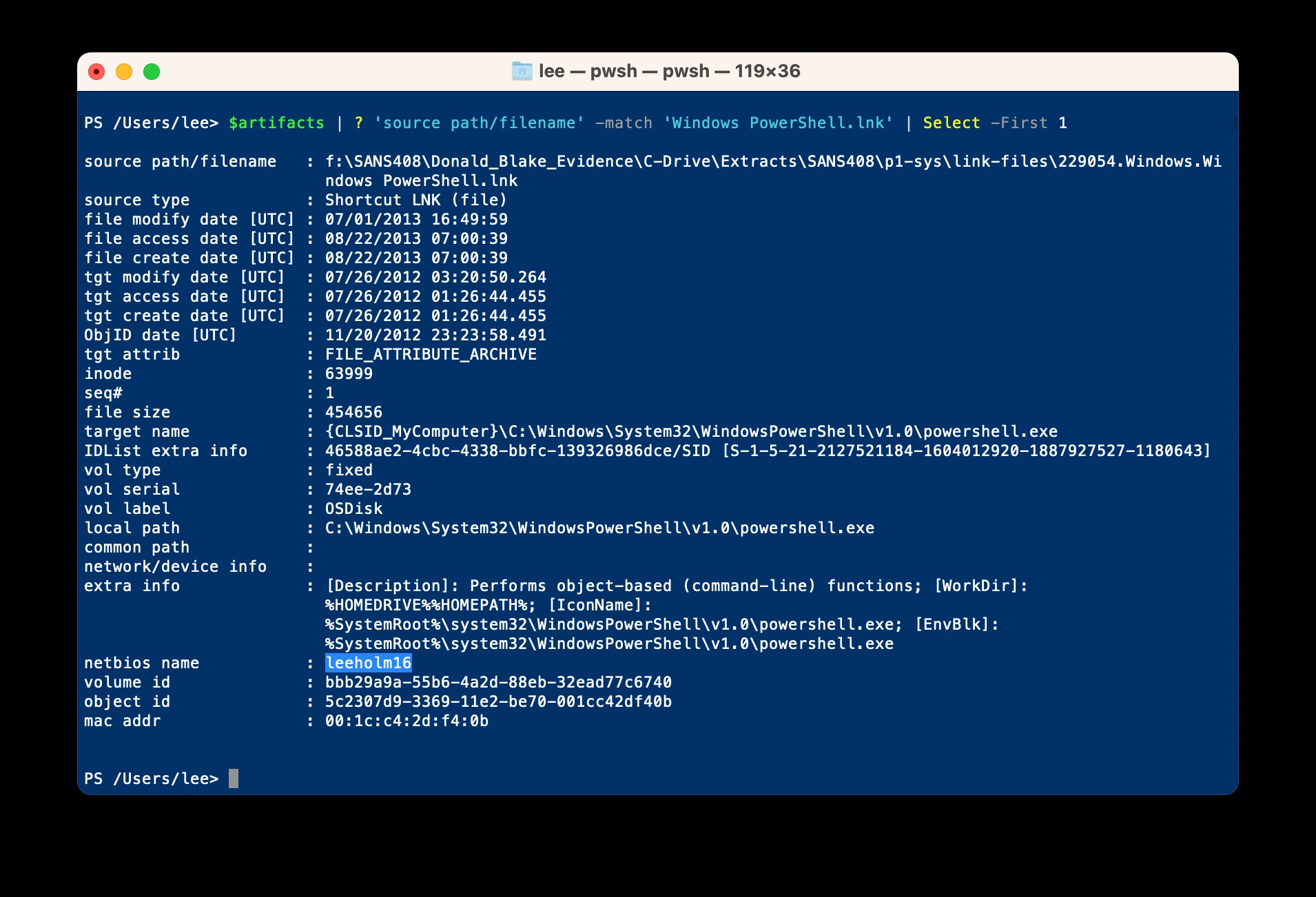
Fortunately for both of us, the reason is not that I (Lee Holmes aka leeholm) hacked your system.
When we were first integrating PowerShell into Windows, one of the bits of work was to create the LNK files that sit in the start menu. For most applications in Windows, the needs are pretty simple (an icon, title, description, and path to launch). The Windows Build has standard ways to make these by calling into the Shell Link COM API.
But in addition to those standard properties, the LNK files for console applications also let you customize things like its font, window size, scroll buffer size, and more. The LNK file for Windows PowerShell tweaks most of these to give an experience fitting of something developed this millenia - PowerShell’s Noble Blue.
Because the COM APIs didn’t support these extended properties, I had to hand edit a LNK file on my dev machine via Explorer to make it how we wanted, and then checked in that file directly.
Unknown to us at the time, Explorer saves the name of the machine doing the editing into the LNK file when you save it. This is what makes that field sometimes interesting when doing forensics on LNK files, but alas it’s nothing more than a history lesson in this case.
